Email scam claiming your account has been compromised
Criminals continue to evolve and find new ways to take advantage of unsuspecting targets. One method that seems to be gaining popularity is for these criminals to simply send an email to their target claiming that they’re already compromised and then demand a ransom in exchange for not doing more (emailing compromising photos to contacts, etc.). From the criminals perspective, it’s much easier (no need to actually ‘hack’ their target, no need to develop ransomware, etc.) and much safer (other than the email, there’s no real trail back to the criminal). From the targets perspective though, as long as they can get past the panic and ‘fight or flight’ stage, it’s much easier to avoid. Below is a screenshot of an email that we received in a honeypot account as an example along with a few dead giveaways that it’s a fake.
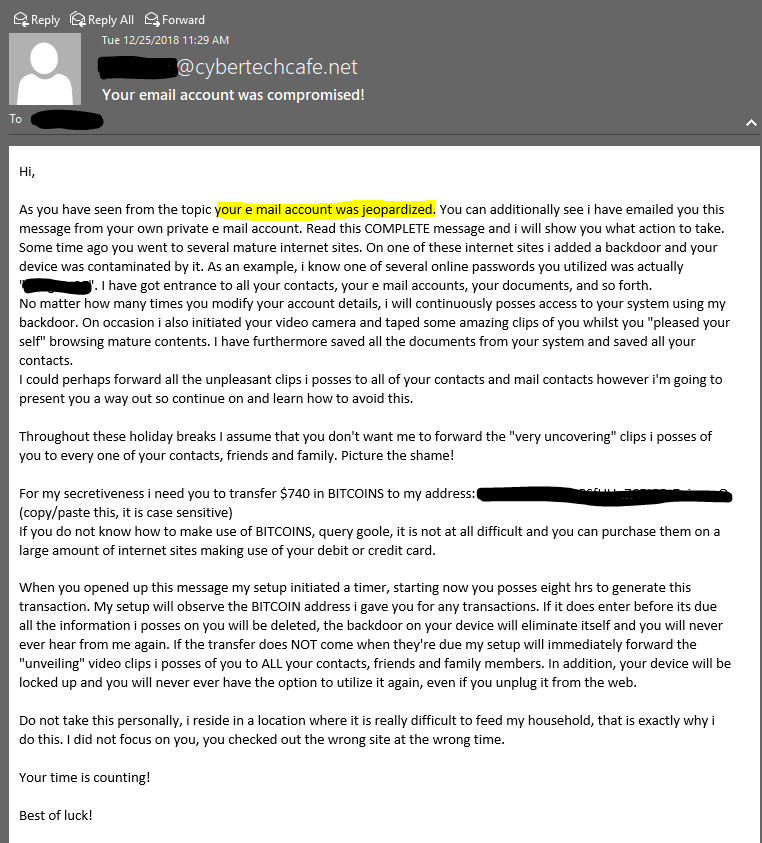
The Message
The Con
- The email is from <email>@yourdomain.com. If your company has properly setup SPF and DKIM records, this would likely never make it to your inbox. That said, you can look at the headers of the message to see if the email originated from your mail server (e.g., was your account compromised) or did it come from somewhere else (more likely the case).
- They have compromising images. The email claims that the criminal has used the targets camera to capture images of the target while they “pleased your self browsing mature contents”. Was there an opportunity for someone to capture you pleasing yourself while browsing mature contents. If not, we can confirm that this is a fraud.
- The Password. The criminal will often use databases of previous password breaches or OSINT to guess at a password that the target may have in the past. Sometimes it’s a legitimate password but more often it’s an old one that was involved in one of countless breaches in the past.
- Panic response. Now that the criminal has your attention (they’ve hacked your email and, with that, they’ve gotten pictures of you pleasuring yourself to mature websites), they’re demanding a sum of money (I’ve seen this as a quantity of Bitcoin or a quantity of US Dollars in Bitcoin).
- Time. You’ve accepted your fate (you’re out $740), now to make sure that you don’t spend time trying to fix it. You’ve got 8 hours to pay or they’ll release the images to all of your contacts.
- Justification. This is basically icing on the cake. Don’t take it personally, they’re just feeding their family.
Summary
If you receive an email that you believe is phishing, it’s always best to error on the side of caution and alert your IT support or IR team per your companies Incident Response Plan so that they can review the message and respond accordingly. If you do not have an IT or IR team and would like information on how Cyber Tech Cafe may be able to help, we’d love to hear from you.

